In 2024, geopolitical instability, marked by conflicts in Ukraine and the Middle East, emphasized the need for stronger cybersecurity in both the public and private sector. China targeted U.S. defense, utilities, internet providers and transportation, while Russia launched coordinated cyberattacks on U.S. and European nations, seeking to influence public opinion and create discord among Western allies over the Ukrainian war. As 2024 ends, we can look back at a hectic cybersecurity landscape on the edge.

2024 marked another record setting year for CVE (Common Vulnerabilities and Exposures) disclosures. Even if many are so-called “AI Slop” reports [1][2], the sheer volume of published vulnerabilities creates a big haystack. As IT security teams seek to find high-risk needles in a larger haystack, the chance of oversight becomes more prevalent. 2024 was also a record year for ransomware payouts in terms of volume and size, and Denial of Service (DoS) attacks.
It also saw the NIST NVD outage, which affected many organizations around the world including security providers. Greenbone’s CVE scanner is a CPE (Common Platform Enumeration) matching function and has been affected by the NIST NVD outage. However, Greenbone’s primary scanning engine, OpenVAS Scanner, is unaffected. OpenVAS actively interacts directly with services and applications, allowing Greenbone’s engineers to build reliable vulnerability tests using the details from initial CVE reports.
In 2025, fortune will favor organizations that are prepared. Attackers are weaponizing cyber-intelligence faster; average time-to-exploit (TTE) is mere days, even hours. The rise of AI will create new challenges for cybersecurity. Alongside these advancements, traditional threats remain critical for cloud security and software supply chains. Security analysts predict that fundamental networking devices such as VPN gateways, firewalls and other edge devices will continue to be a hot target in 2025.
In this edition of our monthly Threat Report, we review the most pressing vulnerabilities and active exploitation campaigns that emerged in December 2024.
Mitel MiCollab: Zero-Day to Actively Exploited in a Flash
Once vulnerabilities are published, attackers are jumping on them with increased speed. Some vulnerabilities have public proof of concept (PoC) exploit code within hours, leaving defenders with minimal reaction time. In early December, researchers at GreyNoise observed exploitation of Mitel MiCollab the same day that PoC code was published. Mitel MiCollab combines voice, video, messaging, presence and conferencing into one platform. The new vulnerabilities have drawn alerts from the Belgian national Center for Cybersecurity, the Australian Signals Directorate (ASD) and the UK’s National Health Service (NHS) in addition to the American CISA (Cybersecurity and Infrastructure Security Agency). Patching the recent vulnerabilities in MiCollab is considered urgent.
Here are details about the new actively exploited CVEs in Mitel MiCollab:
- CVE-2024-41713 (CVSS 7.8 High): A path traversal vulnerability in the NuPoint Unified Messaging (NPM) component of Mitel MiCollab allows unauthenticated path traversal by leveraging the “…/” technique in HTTP requests. Exploitation can expose highly sensitive files.
- CVE-2024-35286 (CVSS 10 Critical): A SQL injection vulnerability has been identified in the NPM component of Mitel MiCollab which could allow a malicious actor to conduct a SQL injection attack.
Since mid-2022, CISA has tracked three additional actively exploited CVEs in Mitel products which are known to be leveraged in ransomware attacks. Greenbone is able to detect endpoints vulnerable to these high severity CVEs with active checks [4][5].
Array Networks SSL VPNs Exploited by Ransomware
CVE-2023-28461 (CVSS 9.8 Critical) is a Remote Code Execution (RCE) vulnerability in Array Networks Array AG Series and vxAG SSL VPN appliances. The devices, touted by the vendor as a preventative measure against ransomware, are now being actively exploited in recent ransomware attacks. Array Networks themselves were breached by the Dark Angels ransomware gang earlier this year [1][2].
According to recent reports, Array Networks holds a significant market share in the Application Delivery Controller (ADC) market. According to the IDC’s WW Quarterly Ethernet Switch Tracker, they are the market leader in India, with a market share of 34.2%. Array Networks has released patches for affected products running ArrayOS AG 9.4.0.481 and earlier versions. The Greenbone Enterprise Feed has included a detection test for CVE-2023-28461 since it was disclosed in late March 2023.
CVE-2024-11667 in Zyxel Firewalls
CVE-2024-11667 (CVSS 9.8 Critical) in Zyxel firewall appliances are being actively exploited in ongoing ransomware attacks. A directory traversal vulnerability in the web management interface could allow an attacker to download or upload files via a maliciously crafted URL. Zyxel Communications is a Taiwanese company specializing in designing and manufacturing networking devices for businesses, service providers and consumers. Reports put Zyxel’s market share at roughly 4.2% of the ICT industry with a diverse global footprint including large Fortune 500 companies.
A defense in depth approach to cybersecurity is especially important in cases such as this. When attackers compromise a networking device such as a firewall, typically they are not immediately granted access to highly sensitive data. However, initial access allows attackers to monitor network traffic and enumerate the victim’s network in search of high value targets.
Zyxel advises updating your device to the latest firmware, temporarily disabling remote access if updates cannot be applied immediately and applying their best practices for securing distributed networks. CVE-2024-11667 affects Zyxel ATP series firmware versions V5.00 through V5.38, USG FLEX series firmware versions V5.00 through V5.38, USG FLEX 50(W) series firmware versions V5.10 through V5.38 and USG20(W)-VPN series firmware versions V5.10 through V5.38. Greenbone can detect the vulnerability CVE-2024-11667 across all affected products.
Critical Flaws in Apache Struts 2
CVE-2024-53677 (CVSS 9.8 Critical), an unrestricted file upload [CWE-434] flaw affecting Apache Struts 2 allows attackers to upload executable files into web-root directories. If a web-shell is uploaded, the flaw may lead to unauthorized Remote Code Execution. Apache Struts is an open-source Java-based web-application framework widely used by the public and private sectors including government agencies, financial institutions and other large organizations [1]. Proof of concept (PoC) exploit code is publicly available, and CVE-2024-53677 is being actively exploited increasing its risk.
The vulnerability was originally tracked as CVE-2023-50164, published in December 2023 [2][3]. However, similarly to a recent flaw in VMware vCenter, the original patch was ineffective resulting in the re-emergence of vulnerability. CVE-2024-53677 affects the FileUploadInterceptor component and thus, applications not using this module are unaffected. Users should update their Struts2 instance to version 6.4.0 or higher and migrate to the new file upload mechanism. Other new critical CVEs in popular open-source software (OSS) from Apache:
- CVE-2024-50379 (CVSS 9.8) in Apache TomCat
- CVE-2024-45387 (CVSS 9.8) in Apache Traffic Control
- CVE-2024-43441 (CVSS 9.8) in Apache HughGraph
- CVE-2024-52046 (CVSS 10) in Apache MINA
The Apache Software Foundation (ASF) follows a structured process across its projects that encourages private reporting and releasing patches prior to public disclosure so patches are available for all CVEs mentioned above. Greenbone is able to detect systems vulnerable to CVE-2024-53677 and other recently disclosed vulnerabilities in ASF Foundation products.
Palo Alto’s Secure DNS Actively Exploited for DoS
CVE-2024-3393 (CVSS 8.7 High) is a DoS (Denial of Service) vulnerability in the DNS Security feature of PAN-OS. The flaw allows an unauthenticated attacker to reboot PA-Series firewalls, VM-Series firewalls, CN-Series firewalls and Prisma Access devices via malicious packets sent through the data plane. By repeatedly triggering this condition, attackers can cause the firewall to enter maintenance mode. CISA has identified CVE-2024-3393 vulnerability as actively exploited and it’s among five other actively exploited vulnerabilities in Palo Alto’s products over only the past two months.
According to the advisory posted by Palo Alto, only devices with a DNS Security License or Advanced DNS Security License and logging enabled are affected. It would be an easy assumption to say that these conditions mean that top-tier enterprise customers are affected. Greenbone is able to detect the presence of devices affected by CVE-2024-3393 with a version detection test.
Microsoft Security in 2024: Who Left the Windows Open?
While it would be unfair to single out Microsoft for providing vulnerable software in 2024, the Redmond BigTech certainly didn’t beat security expectations. A total of 1,119 CVEs were disclosed in Microsoft products in 2024; 53 achieved critical severity (CVSS > 9.0), 43 were added to CISA’s Known Exploited Vulnerabilities (KEV) catalog, and at least four were known vectors for ransomware attacks. Although the comparison is rough, the Linux kernel saw more (3,148) new CVEs but only three were rated critical severity and only three were added to CISA KEV. Here are the details of the new actively exploited CVEs in Microsoft Windows:
- CVE-2024-35250 (CVSS 7.8 High): A privilege escalation flaw allowing an attacker with local access to a system to gain system-level privileges. The vulnerability was discovered in April 2024, and PoC exploit code appeared online in October.
- CVE-2024-49138 (CVSS 7.8 High): A heap-based buffer overflow [CWE-122] privilege escalation vulnerability; this time in the Microsoft Windows Common Log File System (CLFS) driver. Although no publicly available exploit exists, security researchers have evidence that this vulnerability can be exploited by crafting a malicious CLFS log to execute privileged commands at the system privilege level.
Detection and mitigation of these new Windows CVEs is critical since they are actively under attack. Both were patched in Microsoft’s December patch release. Greenbone is able to detect CVE-2024-35250 and CVE-2024-49138 as well as all other Microsoft vulnerabilities published as CVEs.
Summary
2024 highlighted the continuously challenging cybersecurity landscape with record-setting vulnerability disclosures, ransomware payouts, DoS attacks and an alarming rise in active exploitations. The rapid weaponization of vulnerabilities emphasizes the need for a continuous vulnerability management strategy and a defense-in-depth approach.
December saw new critical flaws in Mitel, Apache and Microsoft products. More network products: Array Networks VPNs and Zyxel firewalls are now being exploited by ransomware threat actors underscoring the urgency for proactive patching and robust detection measures. As we enter 2025, fortune will favor those prepared; organizations must stay vigilant to mitigate risks in an increasingly hostile cyber landscape.




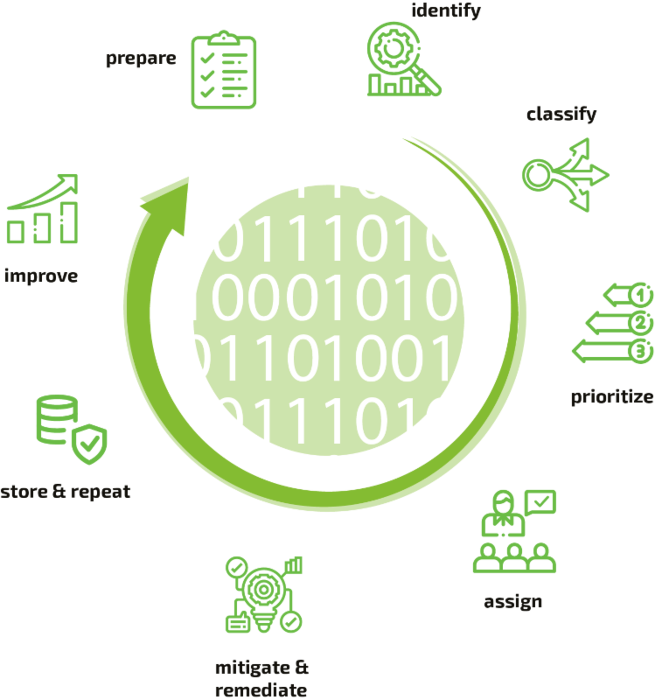 Why Cyber Resilience Is Particularly Important for Critical Infrastructures Sustainable cyber resilience is important for companies in all industries. But it is indispensable in the area of critical infrastructure (CRITIS). As defined by the German government, this includes “organizations or facilities of critical importance to the state community, the failure or impairment of which would result in sustained supply shortages, significant disruptions to public safety, or other dramatic consequences.” CRITIS organizations must therefore protect themselves particularly well against cyber attacks – this is required by law. The EU launched the European Programme for Critical Infrastructure Protection (EPCIP) back in 2006 and expanded and supplemented it in subsequent years. Member states are implementing the EU NIS directive in national law, Germany for instance with the IT Security Act (IT-SIG). Large economic nations have already developed regulatory bodies. In the U.S., for example, this is the National Institute of Standards and Technology (NIST) and in Germany the Federal Office for Information Security (BSI). In Germany, the critical infrastructures are divided into 9 sectors. One of these is the water sector with the divisions of public water supply and wastewater disposal. It includes, for example, waterworks, pumping stations, water pipelines and networks, wastewater treatment plants, the sewerage system, and dam and flood protection facilities. They all play a critical role in our society. Attacks on the water supply could therefore hit a society to the core and, in the worst case, threaten human lives. Attacks on the wastewater disposal system are just as dangerous. If it no longer functions, the result would be considerable hygienic and health problems. Since the water infrastructure uses many IT systems and electronic control systems (ICS) nowadays, it becomes an attractive target for hackers. Incidents Show the Vulnerability of the Water Sector In recent years, there have been numerous attacks on water infrastructures worldwide. Fortunately, there have been no serious consequences so far. However, the attacks show that hackers are exploring how to take control of control systems and prepare further attacks. In 2013, for example, Iranian hackers attempted to penetrate the
Why Cyber Resilience Is Particularly Important for Critical Infrastructures Sustainable cyber resilience is important for companies in all industries. But it is indispensable in the area of critical infrastructure (CRITIS). As defined by the German government, this includes “organizations or facilities of critical importance to the state community, the failure or impairment of which would result in sustained supply shortages, significant disruptions to public safety, or other dramatic consequences.” CRITIS organizations must therefore protect themselves particularly well against cyber attacks – this is required by law. The EU launched the European Programme for Critical Infrastructure Protection (EPCIP) back in 2006 and expanded and supplemented it in subsequent years. Member states are implementing the EU NIS directive in national law, Germany for instance with the IT Security Act (IT-SIG). Large economic nations have already developed regulatory bodies. In the U.S., for example, this is the National Institute of Standards and Technology (NIST) and in Germany the Federal Office for Information Security (BSI). In Germany, the critical infrastructures are divided into 9 sectors. One of these is the water sector with the divisions of public water supply and wastewater disposal. It includes, for example, waterworks, pumping stations, water pipelines and networks, wastewater treatment plants, the sewerage system, and dam and flood protection facilities. They all play a critical role in our society. Attacks on the water supply could therefore hit a society to the core and, in the worst case, threaten human lives. Attacks on the wastewater disposal system are just as dangerous. If it no longer functions, the result would be considerable hygienic and health problems. Since the water infrastructure uses many IT systems and electronic control systems (ICS) nowadays, it becomes an attractive target for hackers. Incidents Show the Vulnerability of the Water Sector In recent years, there have been numerous attacks on water infrastructures worldwide. Fortunately, there have been no serious consequences so far. However, the attacks show that hackers are exploring how to take control of control systems and prepare further attacks. In 2013, for example, Iranian hackers attempted to penetrate the 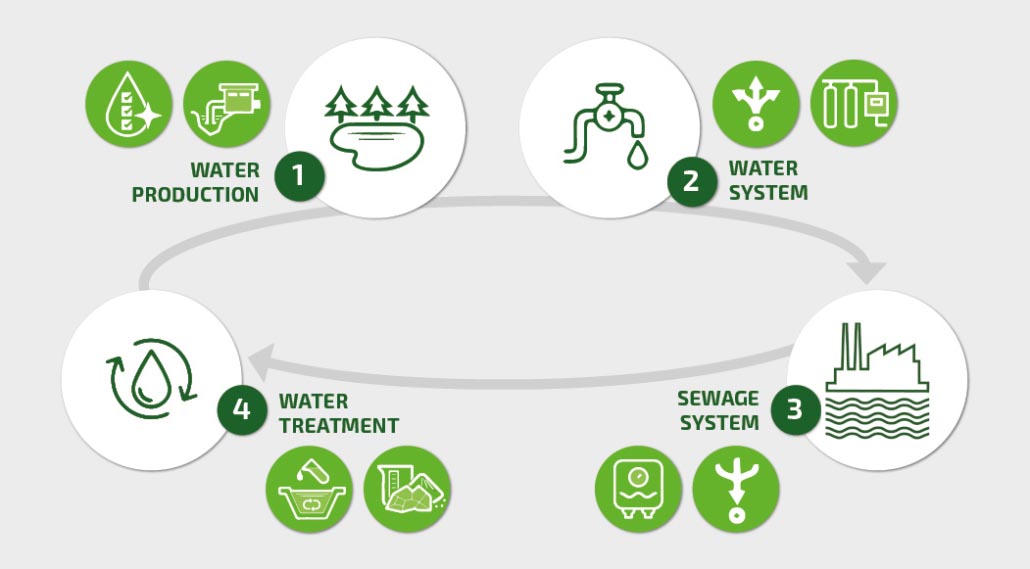 Many networked IT systems and industrial control systems are therefore used in drinking water supply and wastewater disposal, enabling largely automated processes. Examples include sensors for temperature, flow rate, or chlorine content, remotely readable meters, and web portals and mobile apps for customers. Challenges for Cyber Resilience in the Water Sector To reduce their attack surface for cyber criminals, water sector organizations must consider the full range of networked systems, devices and applications. But this is not always easy. One problem is that the ICSs used in the water infrastructure come from different generations. Many of the older control systems were developed at a time when little or no consideration was given to cyber security. This leads to a heterogeneous, vulnerable IT landscape. Additionally, the high degree of automation and dependence on industrial controls makes water infrastructure particularly vulnerable to attack. Furthermore, the IT systems in use are becoming increasingly complex. This makes it difficult for companies to achieve a sufficient level of protection. The increasing networking of components within the field and control level as well as the control and process control technology increases the complexity even further. At the same time, this increases the attack surface for hackers. They have more and more opportunities to penetrate networks, steal data or manipulate industrial controls. Even Previously Unexploited Vulnerabilities Should Not Be Underestimated A recent study by Kenna Security found that the total number of vulnerabilities discovered per year has increased from 4,100 in 2011 to 17,500 in 2021. On the other hand, the percentage of vulnerabilities exploited by hackers has not grown at the same rate. What is the reason for this? Cyber crime follows the same economic rules as any other business model: least investment for maximum result. But cyber crime also suffers from the same problem as the IT industry in general: experts are a limited resource. Companies cannot change this initial situation, but they can ensure that their attack surface is reduced. Tolerating a large attack surface, even if the vulnerabilities are not yet weaponized, is replacing control with gambling. As soon as it seems cheaper for cyber criminals or the outcome is promising, cyber crime will focus on vulnerabilities that are not yet weaponized, and the conversion of vulnerabilities into weapons will happen quickly. Even worse is the motivation of cyber terrorists, who have so far been fortunately unsuccessful due to a lack of expertise. It is unclear whether they will gain the necessary skills and if so, when. But they do not follow the rules of economics, which makes them less predictable in selecting targets and suitable weaponized vulnerabilities. In essence, there are two good general reasons why organizations should establish a process to manage and minimize their entire attack surface and not just focus on current (or likely) weaponizable vulnerabilities:
Many networked IT systems and industrial control systems are therefore used in drinking water supply and wastewater disposal, enabling largely automated processes. Examples include sensors for temperature, flow rate, or chlorine content, remotely readable meters, and web portals and mobile apps for customers. Challenges for Cyber Resilience in the Water Sector To reduce their attack surface for cyber criminals, water sector organizations must consider the full range of networked systems, devices and applications. But this is not always easy. One problem is that the ICSs used in the water infrastructure come from different generations. Many of the older control systems were developed at a time when little or no consideration was given to cyber security. This leads to a heterogeneous, vulnerable IT landscape. Additionally, the high degree of automation and dependence on industrial controls makes water infrastructure particularly vulnerable to attack. Furthermore, the IT systems in use are becoming increasingly complex. This makes it difficult for companies to achieve a sufficient level of protection. The increasing networking of components within the field and control level as well as the control and process control technology increases the complexity even further. At the same time, this increases the attack surface for hackers. They have more and more opportunities to penetrate networks, steal data or manipulate industrial controls. Even Previously Unexploited Vulnerabilities Should Not Be Underestimated A recent study by Kenna Security found that the total number of vulnerabilities discovered per year has increased from 4,100 in 2011 to 17,500 in 2021. On the other hand, the percentage of vulnerabilities exploited by hackers has not grown at the same rate. What is the reason for this? Cyber crime follows the same economic rules as any other business model: least investment for maximum result. But cyber crime also suffers from the same problem as the IT industry in general: experts are a limited resource. Companies cannot change this initial situation, but they can ensure that their attack surface is reduced. Tolerating a large attack surface, even if the vulnerabilities are not yet weaponized, is replacing control with gambling. As soon as it seems cheaper for cyber criminals or the outcome is promising, cyber crime will focus on vulnerabilities that are not yet weaponized, and the conversion of vulnerabilities into weapons will happen quickly. Even worse is the motivation of cyber terrorists, who have so far been fortunately unsuccessful due to a lack of expertise. It is unclear whether they will gain the necessary skills and if so, when. But they do not follow the rules of economics, which makes them less predictable in selecting targets and suitable weaponized vulnerabilities. In essence, there are two good general reasons why organizations should establish a process to manage and minimize their entire attack surface and not just focus on current (or likely) weaponizable vulnerabilities:

